CHIRP: Cloud Hypervisor Forensics and Incident Response Platform
CHIRP is a cloud forensics platform that empowers analysts and defenders to collect evidence and incident response materials in real-time without disturbing the user environment or alerting the intruder.
With more than 92% of enterprises now having a cloud presence and the frequency of large-scale data breaches rising over 273% year-over-year, does your organization have the tools to know whether and how it has been breached?

The widespread adoption of enterprise cloud computing and Infrastructure-as-a-Service (IaaS) poses challenges for cyber incident response and forensics teams investigating not only breaches and leaks, but also cyber-crime in cloud environments. As cloud computing and IaaS become more ubiquitous, so does the need for tools that can conduct effective cloud forensics and incident response.
Due to the ephemerality, location, and issues with ownership of the data, disks, and technology provided by Cloud Service Providers (CSPs), cloud-based entities and cloud customers have struggled to establish foundational forensic capabilities to reduce security risks. Even further, IaaS platforms rely on hypervisors to virtualize computer systems, but most do not offer a useful Application Programming Interface (API) to support customizable, contextual introspection which is what an analyst needs to conduct investigations.
A more global cloud forensics solution is needed that can provide instrumentation with minimal overhead, common data models, and collection of broad data sets. A virtual machine (VM), hypervisor, and operating system agnostic solution would offer needed versatility for varied enterprise infrastructures. A solution that encompasses these features could enable analysts to better address current issues in enterprise cybersecurity.
Sandia’s Approach: CHIRP
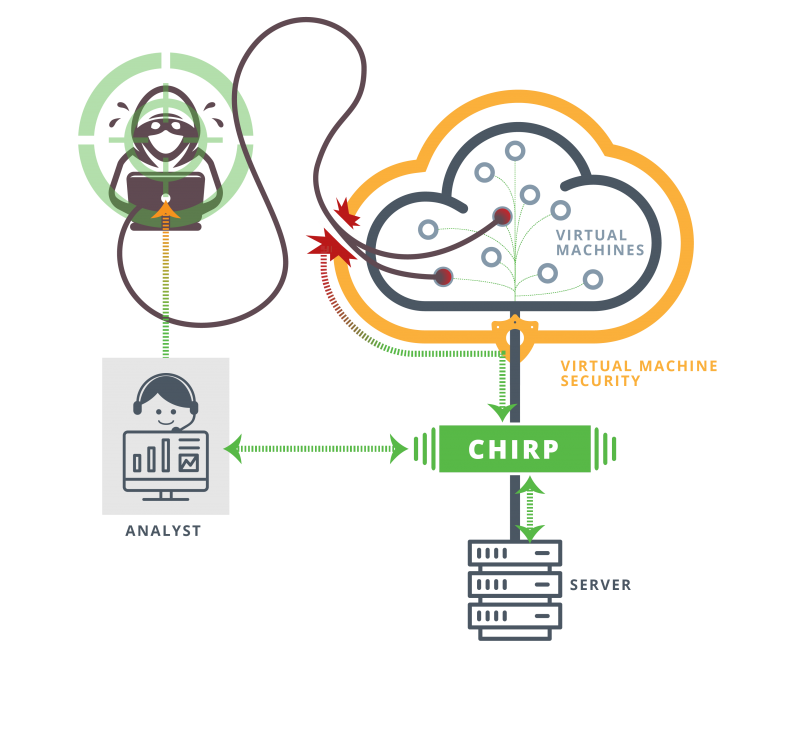
Sandia’s Cloud Hypervisor Forensics and Incident Response Platform (CHIRP) introduces a custom Virtual Machine Introspection (VMI) based approach to provide intelligence and forensic artifacts from active VMs in cloud systems. This platform agnostic solution involves significantly lower overhead than comparable solutions. Its ability to collect text and binary data allows correlation with other sources. Typically, hypervisor-based solutions abstract underlying computer hardware from operating systems running on virtual machines. Instrument virtual machine solutions (VMs) place an extra load that attackers can detect or even influence. Instrument hypervisors such as CHIRP provide an advantageous solution where the attacker cannot detect monitoring. Using CHIRP, analysts can pinpoint suspicious activities, track and record attacker actions for forensic analysis, and may retrieve materials transparently from the targeted machines automatically or on-demand. These extractions occur in real-time without affecting or alerting the intruder to the detection.
CHIRP offers a broader set of features compared with current commercial offerings. Designed for IaaS applications from the start, CHIRP provides a platform and OS agnostic solution with much lower overhead. Compared with other existing solutions, CHIRP is lightweight and can provide a real-time dynamic response. Its configurable logging delivers insights for meaningful incident response or forensics.
Large or complex organizations such as government agencies, providers of cloud service or managed services as well as cybersecurity forensics and enterprise security operations teams may benefit from the versatile features and capabilities of Sandia’s CHIRP solution.
| Software Title | Date |
|---|---|
| CHIRP: Cloud Hypervisor Forensics and Incident Response Platform | 04/08/2020 |
SCR# 2278
Published10/1/2021
Last Updated10/1/2021
